In 2010 John Kindervag created the Zero Trust Network or Zero Trust Architecture; while he was a principal analyst at Forrester Research Inc., Zero trust is now a standard from NIST; it is NIST SP 800-207. Zero trust is a model for more effective security that is desperately needed in today’s threat landscape.
What is Zero Trust?
In information security, trust is a bad word. If you ask security professionals today to trust someone/something, the answer will not be favorable. It should be difficult for security professionals to trust. It is part of the job. Carry that idea to all of our networks and environments, and you end up with the concept of Zero Trust.
Why Zero Trust? Think about these breaches
The 2020 Data Breach Study, conducted by Ponemon Institute and sponsored by IBM, found that the global average cost of a data breach is $2.4 million. Although that figure is down from the prior year’s number, the study found that the average size of the data breaches decreased to more than 12,000 records.
Organizations continue to spend more and more money on security technology, licenses, and training. Gartner Inc., a tech research and advisory firm, identified spending worldwide on information security products and services was at $123.8 billion in 2020, up 2.4 percent over 2019.
Information Security Evolved
The traditional concept of establishing perimeters and defining them with firewalls to create a boundary that determines where you trust (inside) and do not (outside) no longer works. Today, some of the most significant breaches have occurred because a hacker gained access to someone’s account credentials and moved laterally within the business.
Especially with cloud environments today, there is a great deal of trust that DevOps give to accounts and profiles. Once the attacker can obtain access to one of those accounts, they can then move laterally or east to west through the business. Then there will be a data breach.

One of the best examples today is Ms. Paige Thompson and her theft of over 100,000 data files from Capital One that contained personal data, including social security numbers, addresses, phone numbers, and more. That breach was possible because the account named ‘****-WAF-Role’ was given ‘List buckets Command’ and the ‘Sync command.’ The web application firewall administrator should not have permission to find and look through data buckets. Capital One has confirmed that someone should not have enabled those permissions.
Networks Grow and Evolve
The network environment that we have today is dramatically different from even just a few years ago. We no longer have a corporate data center with all of our servers and services held within. We now have cloud services that store our data in many different locations, from Microsoft365 (formerly Office365) to Salesforce and on to Dropbox and more. It is necessary to rethink our designs, equipment, and logic to secure our business and not experience a data breach. Bad actors and malicious threats aren’t the only factors driving this new model.
The technologies behind Zero Trust
Securing an enterprise IT environment with the Zero Trust approach requires our security governance to be modified and our technology to change and grow with our different environments.
Micro-segmentation is one of the first changes that we need to make. We have slowly evolved the size of networks and subnets to smaller and smaller groupings of devices. We then work to patch and remediate all vulnerabilities while trying to control access. This approach, while helpful, leaves us trying to play catchup as we work to secure the devices within a subnet as we learn of vulnerabilities and work to test the patches before installation.
Suppose we approach things from a different perspective by starting with tiny isolated environments. Then work to know who and what needs access before moving forward. If we do that, we will have a better chance of controlling that access.
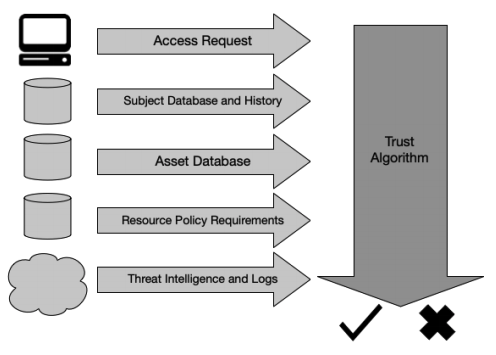
We must understand who the user is. Let’s make sure we know what endpoint the user is coming from – is it a known secure endpoint, and what is the security status is of that endpoint? Add a conditional policy dictating what someone can access.
For this to work, technologies we have had for some time are still employed. Technologies such as Identity and Access Management (IAM), analytics, file system permissions, multi-factor authentication (MFA), and encryption, to name but a few, are still used.
We must still use the concept of least privilege to govern our access decisions. If we change our perspective from “What access does this user need” to “Who needs access to this resource,” we might have a better chance of information security. Ask who needs access to this database to do their work and why? Rather than asking what access does Omar require?
How to Start with Zero Trust
So many of our traditional technologies are still in use within Zero Trust; multi-factor authentication, least privilege, and so on, so the question is what’s different. The answer is in perspective. The user and end device will not be granted access until they prove that we can trust them. Who is the user, what is their background, what work are they doing, what machine are they using, what level of confidence do I have in this user are but some of the questions to ask
Zero Trust is not an easy or quick change to make. Retraining our brains to refuse access until we know that it is safe to do so takes much work. Changing our existing environments is also not a quick process.
However, as we move into the cloud, it would be a perfect time to start our builds from this perspective. Build from Zero Trust do not retrofit an environment. Developers and operations will struggle to change their thoughts and practices to build from Zero Trust out. Vendor default configurations grant a fair amount of access to not annoy customers with products that require a large amount of work to get started.
We also have to modify our view. Most DevOps personnel believe that our firewalls will keep people out. The problem is that the bad actors are already past the firewall; they are already in our networks. We need to control movement by locking environments down.
Most importantly, the move to Zero Trust should be from the top down. The Board of Directors, the CEO, CIO, and CISO must support and guide the process.