The Solution We Turn To That Bad Actors Abuse
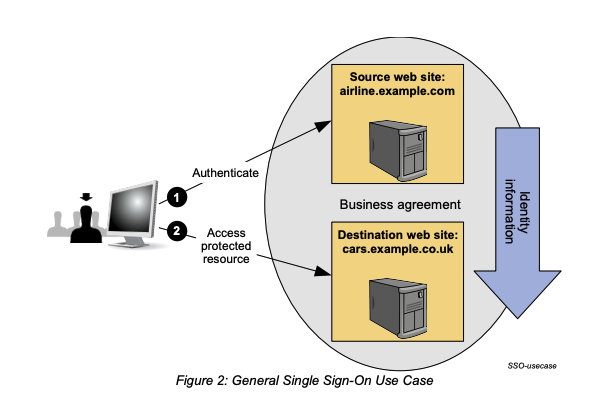
Security Assertion Markup Language (SAML) has been around for many years and is commonly used for federated Single Sign-On (SSO). Bad actors have been abusing the trust that we place in these systems for some time. The National Security Agency (NSA) released a cybersecurity advisory at the end of 2020 regarding two specific attack techniques to be concerned with today. Bad actors are exploiting on-prem systems initially that allow them access to SAML authentication services. What is critical to point out is that SAML is not the attack point; it is not a compromise of SAML tokens themselves. The attacks are aimed at systems around the federated SSO structure.

In the first attack technique, bad actors will compromise an element of a federated SSO infrastructure. Once that system is compromised, they steal the credentials or private key used to sign SAML tokens. As a variation of that, if the bad actor cannot obtain the signing key, they elevate their permissions to add a malicious certificate trust relationship that allows the creation of forged SAML tokens.
The second attack technique being used today involves compromising a global administrator account. Once that account is compromised, they assign credentials to cloud application service principals. That principal is an identity used for cloud applications when the application requires access to other cloud resources. As a result, if the bad actor can create these service principals, they can then access those resources themselves.
Protect Critical Resources with Hardening
Hardening systems are the place to start to protect critical resources; this is nothing new in Information Technology (IT) or Information Security (IS). The steps to take may differ than traditionally, but the idea is still the same. When a system is hardened, we make it harder for the bad actor to gain access. General hardening steps involve keeping the system patched, ensuring that all unnecessary services are shut down, unnecessary ports are closed, and so on. When it comes to federated SSO and these two attack techniques, there are specific things to ensure.
- Utilize strong authentication-which today is multi-factor (MFA) or two-factor authentication (2FA).
- Ensure that token claims are consistent with the organization’s policy.
- Review all access granted to applications for excessive or unneeded access levels so that administrators can remove them.
- Monitor privileged identities, their access, and their changes and respond to any suspicious activity immediately.
Monitor Critical Assets
It is critical to watch over on-prem and cloud systems to protect our critical assets. Monitoring systems are also not a new idea, but what we need to watch for within federated SSO involves:
- Tokens that have unusually long lifetime
- Token claims that do not match the organization’s policy.
- Token authentication claims that do not match the organization’s methods.
- Tokens that access a cloud resource that when mapped to identity provider logs does not have a creation entry.
It is exceptionally critical that we monitor privileged identities and principals. It is necessary to watch for suspicious activity taken by administrator accounts or activities related to service principal accounts.
Contact us to discover how our crowdsourced security platform can aid in protecting your company from the ever-present threats and vulnerabilities to your online applications.