HIPAA, the Health Insurance Portability and Accountability Act, is a US federal law designed to protect patient data. When electronic protected health information is exposed due to security failures, enforcement actions can be severe. In recent years, fines exceeding $10,000,000 have been issued to healthcare organizations that failed to adequately safeguard sensitive data. Beyond financial penalties, organizations must also demonstrate to auditors and accreditation bodies that they have effective security controls in place. For many healthcare providers, testing with compliance-reading reporting is a critical requirement, but the real value comes from identifying and fixing vulnerabilities before they lead to a breach.
Today, many healthcare organizations rely on penetration tests or bug bounty programs primarily to demonstrate readiness during audits. While this can satisfy short-term compliance needs, it often leaves deeper security gaps unaddressed. Preparing only for an audit is similar to tidying up before visitors arrive. Everything may look acceptable on the surface, but underlying issues remain.
For healthcare organizations approaching an accreditation review or working to strengthen their HIPAA security posture, security testing works best when it is continuous, realistic, and aligned with compliance goals. A more integrated approach helps reduce long-term risk while providing the defensible evidence that auditors expect.
How Adaptive Security Tests Defend Against Today's Real-World Threats
HIPAA’s Security Rule requires safeguards that remain effective against current and emerging threats. A vulnerability scan performed months ago may fail to detect a critical zero-day exploit actively targeting an electronic health record system today.
To meet this standard, security testing must evolve alongside the threat landscape facing healthcare organizations. Ongoing penetration testing, targeted assessments, and responsibly managed vulnerability disclosure or bug bounty programs help organizations identify real-world attack paths as they emerge. These efforts provide evidence that protections for electronic protected health information are not only compliant in documentation, but resilient in practice. For auditors and regulators, this kind of testing supports stronger confidence in both technical controls and risk management processes.
Integrating Security Readiness into Board-Level Reporting and Audit Workflows
Security readiness must be communicated clearly to executive leadership and oversight bodies, not just measured by technical teams. For healthcare organizations, this means translating security testing results into reporting that boards and audit committees can understand and act on. Well-integrated reporting connects identified risks to potential operational, financial, and regulatory impact while documenting remediation efforts over time. When security findings are incorporated into regular audit workflows, leadership gains visibility into how risks to electronic protected health information are being managed, enabling informed governance decisions and demonstrating organizational accountability during regulatory reviews.
Leveraging Managed Security Programs to Reduce Risk and Demonstrate Compliance
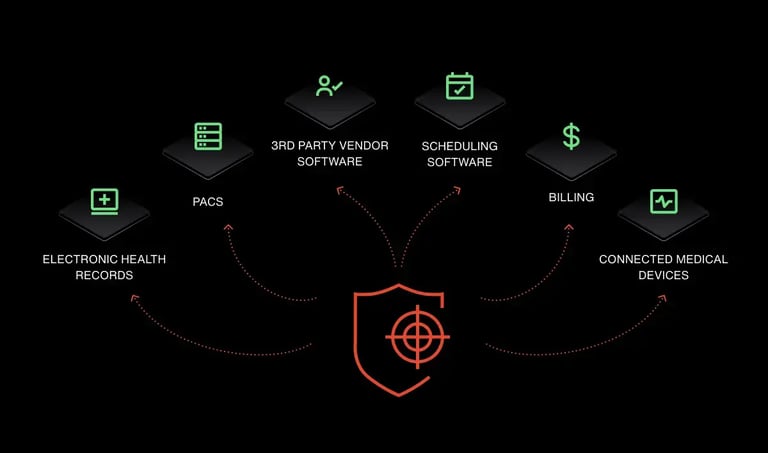
Even organizations that do not sell directly to large technology companies still rely heavily on third party vendors such as billing platforms, cloud service providers, and specialized imaging systems. These partners need assurance that the handling of protected health information will not introduce additional risk or compromise their own compliance obligations.
When a healthcare organization completes a comprehensive penetration test or a time bound security testing program with validated remediation, independent confirmation of that work can provide meaningful assurance to vendors and partners. Documented evidence of testing scope, findings, and resolution helps demonstrate that security controls are not only in place, but actively maintained.
This type of verified assurance supports smoother vendor onboarding and integration by reducing friction during security reviews. By establishing trust earlier in the process, organizations can accelerate the deployment of critical systems and services while reinforcing confidence in how patient data is protected across the broader healthcare ecosystem.
Security That Supports Your Mission
For healthcare organizations facing increasing regulatory scrutiny and real-world cyber risk, Inspectiv provides a practical and effective path forward. In one recent healthcare engagement, a critical vulnerability was identified during the initial testing phase, only weeks after onboarding. Findings like these underscore how quickly meaningful risk can surface when testing reflects real attacker behavior.
Inspectiv pairs rigorous, adaptive security testing with an understanding of healthcare constraints, delivering depth without unnecessary cost and support that aligns with how compliance and security teams actually operate. This approach enables organizations to strengthen their HIPAA posture with confidence, protect patient data, and preserve the trust that patients and partners depend on.
If your organization is ready for security testing that balances realism, affordability, and compliance readiness, talk to Inspectiv today.