Bug Bounty, Simplified
Find and fix the highest-risk vulnerabilities in your ecosystem, leveraging a community of skilled researchers.


A Better Bug Bounty
Inspectiv’s Bug Bounty as a Service acts as an extension of your security team, leveraging a community of skilled researchers to find the most high-risk vulnerabilities in your ecosystem. The Inspectiv platform makes it clear which vulnerabilities are priorities, and replicates every vulnerability, providing clear remediation instructions. Flat-fee pricing means budgeting is a breeze.
Free your team from the noise so they can focus on what’s most important.
Product Benefits
Continuous Risk Reduction
A curated community of skilled researchers matched to your needs are deployed around the clock to find your most impactful vulnerabilities.
Save Time
The Inspectiv platform prioritizes vulnerabilities and provides clear remediation instructions. And Inspectiv handles all researcher management and communications, so your team can focus on remediation and strategy.
Start Small or Go Big
With Inspectiv, you can scope your programs in whatever way works best for your organization, and subsidiaries can launch independent of each other, offering total flexibility.

Predictable Costs
Inspectiv handles all researcher bounty determinations and payouts, and offers customers a fixed pricing model. No more escrow accounts or unpredictable budgets - you know exactly what you’re paying.
What is Bug Bounty?
Inspectiv’s Bug Bounty as a Service acts as an extension of your security team, leveraging a community of skilled researchers to find the most high-risk vulnerabilities in your ecosystem. Bug Bounty programs pay reward “bounties” to ethical hackers who find and report vulnerabilities in your app, website, or other digital infrastructure.
What makes Inspectiv Bug Bounty as a Service different?
Inspectiv BBaaS fixes the biggest pain points of traditional Bug Bounty programs — so your team is free to focus on what’s most important. You won’t need to devote internal resources to managing researchers, and flat-fee pricing means budgeting is a breeze.
A Curated Researcher Community
Extend the reach of your internal security team — without managing outside resources.
Our community of skilled researchers hunts around the clock for the most impactful vulnerabilities in your web and mobile apps and APIs. Researchers are matched to your program, ensuring the right skill set is deployed for your needs. Inspectiv works closely with its researcher community, handling all researcher communications so that our customers can focus on strategy and vulnerability remediation.
Get a Demo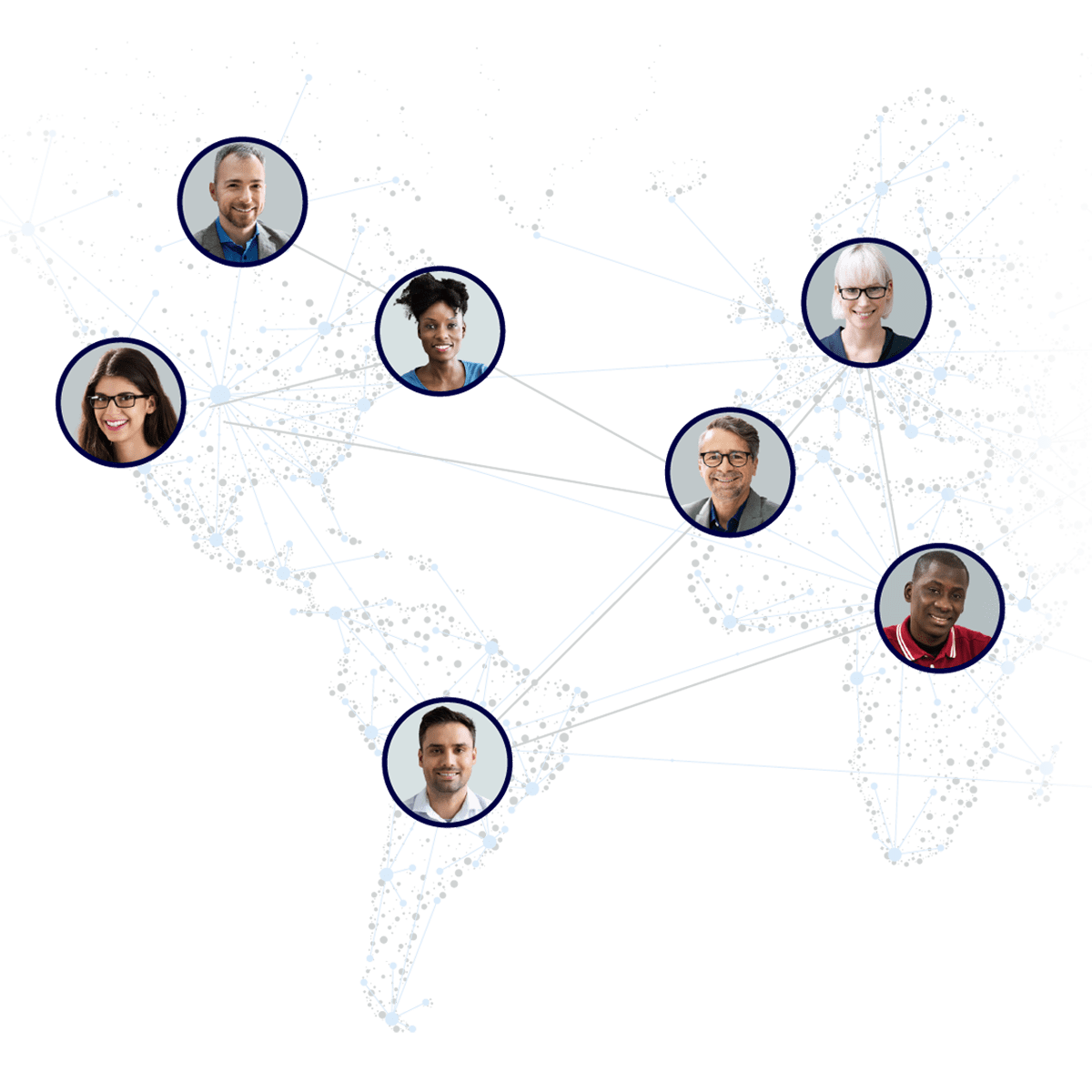
The Best Triage in the Business. Period.
Inspectiv goes beyond the typical triage provided by other bug bounty providers to deconstruct and replicate vulnerabilities, collaborate with researchers, and ensure your team has the precise instructions they need for successful threat remediation.
Get a Demo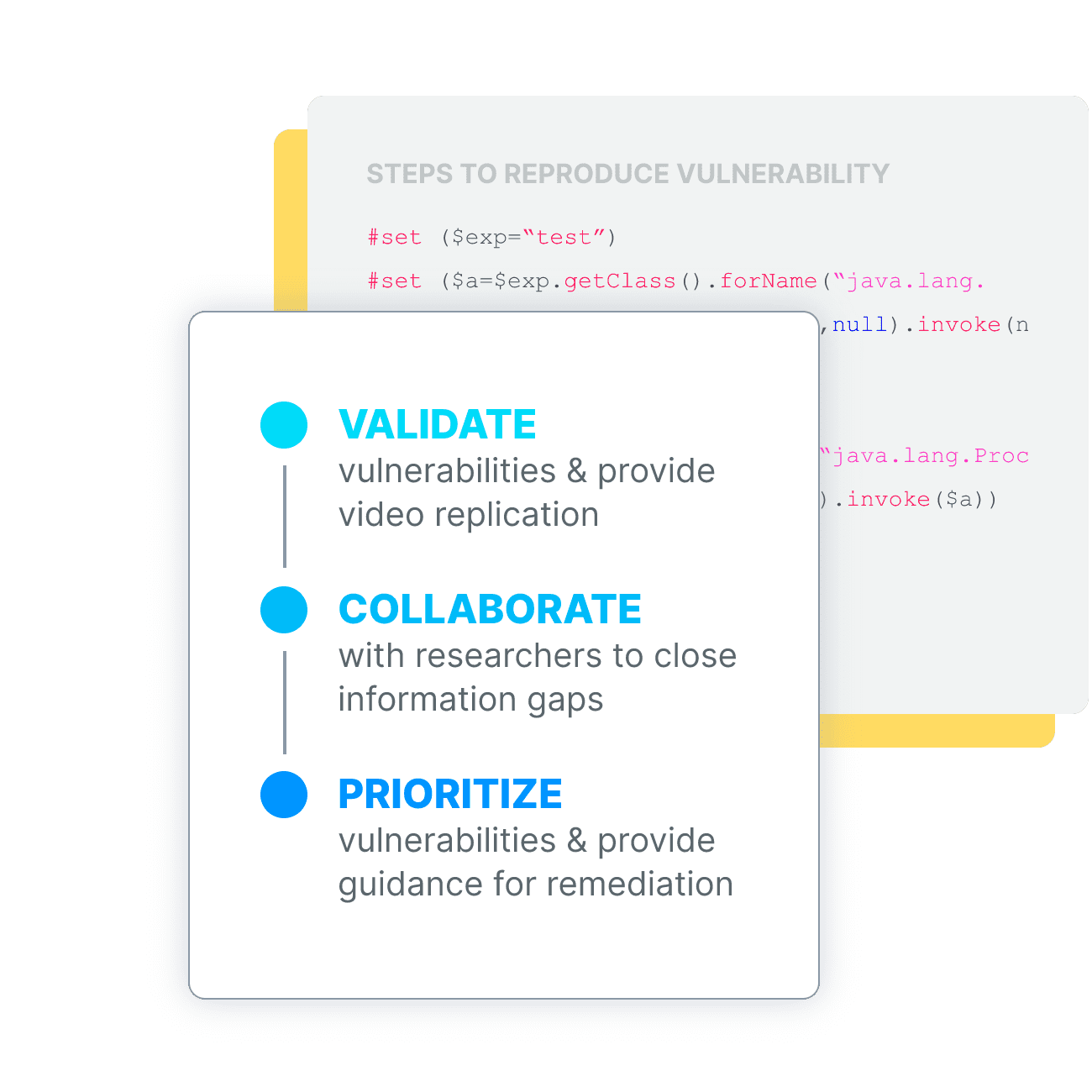
Transparent, Subscription Pricing
Inspectiv’s flat-fee subscription model means you know exactly what to budget today and into the future as you scale up your bug bounty programs — no more guesswork. Inspectiv works with researchers directly to determine bounty incentives, and handles all payouts, eliminating the need for escrow accounts inherent to other bug bounty programs
Get a Demo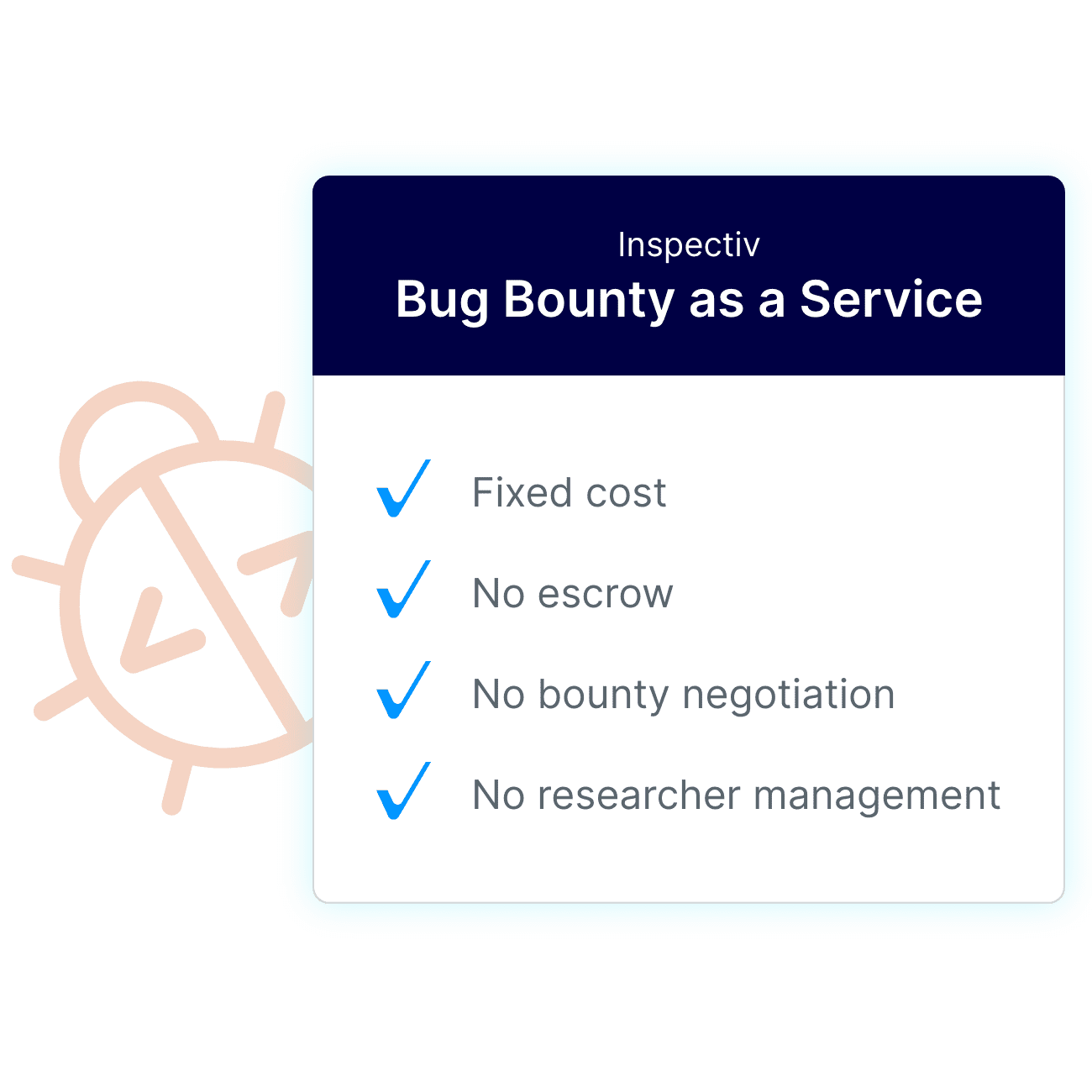
PTaaS and BBaaS: What’s the Difference?
Pentesting and Bug Bounty are complementary services that, combined, ensure you meet your compliance needs while strengthening your security posture through continuous risk reduction.

|

|
|
|---|---|---|
| Primary Benefit |
Continuous Risk Reduction; Removal of Complex Security Vulnerabilities |
Compliance-Driven Security Testing |
| Testing Approach |
Grey Box + Black Box testing; only vulnerabilities reported |
Methodology Driven |
| Timing | Continuous | Time-Boxed |
| Testers | Researcher Community | Internal Security Team |
| Scope |
Web & Mobile Applications; APIs |
Active Directory; Cloud Security Embedded Softwares & IoT External & Internal Network Testing Red Team Assumed Breach Web & Mobile Applications; Web Infrastructure; APIs Wireless Assessments (incl’d Rogue Network Detection) |
|
Vulnerability Discovery |
Yes | Yes |

Removal of Complex Security Vulnerabilities
only vulnerabilities reported
APIs
Discovery

Embedded Softwares & IoT
External & Internal Network Testing
Red Team Assumed Breach
Web & Mobile Applications; Web Infrastructure; APIs
Wireless Assessments (incl’d Rogue Network Detection)
Discovery
Bundle your Bug Bounty with Pentesting as a Service for continuous risk reduction
Ready to get started with Inspectiv Bug Bounty as a Service?
Get a personalized demo
Get all your questions answered in a quick 30-minute walk through with our team.


