Platform
Explore Inspectiv’s AI-enabled platform that integrates Bug Bounty, Pentesting, Feature Testing, and VDP, designed to cut through noise and deliver signal-driven results.
Platform
Explore Inspectiv’s AI-enabled platform that integrates Bug Bounty, Pentesting, Feature Testing, and VDP, designed to cut through noise and deliver signal-driven results.
Bug Bounty
Continuously discover high-impact vulnerabilities, without the overhead of traditional bug bounty programs.
Penetration Testing
Stay audit-ready and reduce risk with expert-led testing and flexible retesting support.

See Inspectiv in Action!
Schedule a live demo to see how our platform helps you manage vulnerabilities, reduce noise, and stay compliant.

See Inspectiv in Action!
Schedule a live demo to see how our platform helps you manage vulnerabilities, reduce noise, and stay compliant.

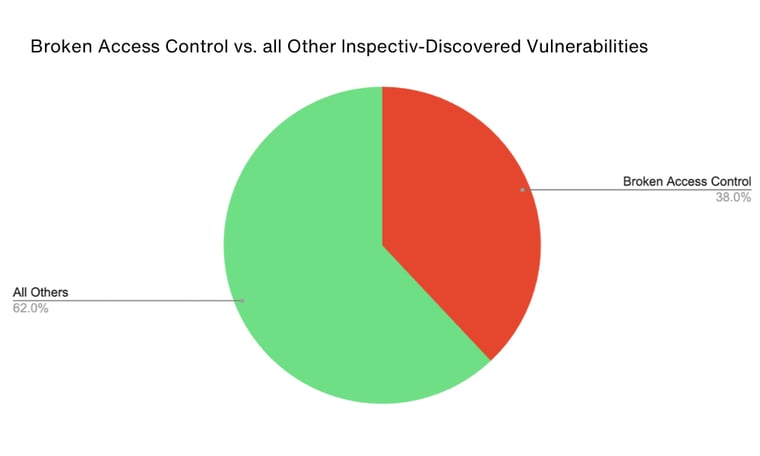
Every year, the OWASP Top Ten highlights the most critical security risks facing web applications. Until the late 2025 update from OWASP, the #1 category remains Broken Access Control and Inspectiv’s own bug bounty data tells the same story. Across our bug bounty programs, vulnerabilities tied to improper access control are the most frequently reported issue by security researchers comprising 38% of our vulnerabilities.
This alignment between OWASP’s global findings and Inspectiv’s platform data underscores a simple truth: access control is hard, even for experienced teams. Modern development practices including continuous deployment, distributed architectures, and fast-moving product cycles make it easier than ever to introduce subtle authorization flaws.
In this article, we’ll unpack why broken access control is so pervasive, how organizations can detect it before attackers do, and what steps lead to long-term, resilient remediation.
At its core, access control determines who can do what within an application. It enforces the boundaries between user roles, data sets, and system functions. When these boundaries fail, attackers can act outside their permissions viewing other users’ data, modifying records, or escalating privileges.
Inspectiv’s vulnerability data shows that these flaws appear across every industry and tech stack. Why? Because access control is tightly tied to each app’s unique business logic. Unlike SQLi or XSS, there’s no universal pattern to catch. Every product defines “who should have access” differently, so every implementation becomes a custom solution and therefore a potential source of bugs.
Three realities amplify the problem:
A few anonymized examples from Inspectiv’s bug bounty programs illustrate how these vulnerabilities manifest:
Each represents a unique breakdown in authorization logic not a technical exploit, but a design oversight.
Preventing these issues requires visibility and consistent testing. Based on Inspectiv’s experience running large-scale vulnerability programs, the best approach combines several layers:
Together, these layers create a continuous feedback loop between your developers and the security community ensuring you find issues before attackers do.
When a broken access control vulnerability is reported, the instinct is to “patch the hole.” But quick fixes rarely address the deeper cause of inconsistent or decentralized authorization logic.
The more sustainable solution is to redesign your access model with security at its core:
This approach takes more upfront effort, but it pays dividends. Teams that re-architect access control systems save time and resources in the long run by eliminating recurring vulnerabilities and reducing reliance on reactive fixes.
Broken Access Control remains the most common vulnerability because it’s the most human embedded in custom business logic, rushed deployments, and evolving architectures. Our bug bounty data confirms what OWASP has long warned: authorization is one of the hardest things to get right.
But it’s also one of the most preventable. With continuous testing, clear visibility into architecture, and a commitment to secure design, organizations can break the cycle of recurring access control bugs.
At Inspectiv, we help security and engineering teams operationalize this mindset. Our platform connects customers with expert researchers who test what automation can’t providing actionable findings, real-time insight, and validation that your controls work as intended. Book a demo to see how continuous security testing can help you eliminate critical vulnerabilities before they reach production.
Access control may be complex, but securing it doesn’t have to be chaotic. With the right visibility and testing cadence, you can move fast and stay secure.
Ready to level up your AppSec program? Book a personalized demo to see how Inspectiv helps you uncover real risks, streamline workflows, and scale your security program through one unified platform designed to operate the way your team does.



